Building a Comprehensive Digital Executive Protection Program
Executive Protection has evolved beyond physical security to encompass the protection of executives' digital lives.

Building a Comprehensive Digital Executive Protection Program
Executive Protection has evolved beyond physical security to encompass the protection of executives’ digital lives. With the increasing sophistication of cyber threats, building a robust digital executive protection program has become a necessity for safeguarding executive leadership teams and their organizations. This article provides a comprehensive guide to build a tailored program for your organization.
What is Digital Executive Protection
Executive protection is essential in today’s digital age, to ensure the integrity of executive leadership teams. Digital Executive Protection programs safeguard everything digital, and mitigate the risks associated with reputational harm, financial impact, erosion of confidence, and potential disruption to business continuity.
Every program is different, tailored to unique variables within the organization such as size, risk tolerance, threat landscape, resources, and security charter.
A simple program can consist of data broker removal and a password manager. A more sophisticated program can include a complete hybrid model with an in-house digital security team leverages the expertise and resources of an outsourced provider. There is no right and wrong, there is simply risk and risk mitigation.
Digital Risks to Executives
In the realm of corporate security, understanding and mitigating executive risk is a top priority. As security professionals, it’s crucial to be aware of the potential consequences that executive leadership teams face, such as reputational harm, financial impact, erosion of confidence, and disruption to business continuity. The implications of these risks can be far-reaching, affecting not only the executives themselves but also the overall stability and success of the organization.
A Digital Executive Protection Program mitigates digital and physical risks:
- Account Takeover
- Malware and Spyware
- Reputational Harm
- Financial Impact
- Business Continuity
- Technical Surveillance
- Corporate Espionage
In this guide, we go deep into what it takes to build a Digital Executive Program to mitigate the modern executives’ risk.
Best Option, In-house or Outsource?
One of the first evaluations to consider is whether to build an inhouse team, a hybrid model, or completely outsource the program. There are pros and cons to each model, here is a quick chart to help determine which course would be the best option:
| Model | Pros | Cons |
| In-house | ||
| Hybrid | ||
| Outsourced |
Who is Digital Executive Protection For?
Digital Protection is for high profile individuals:
- Executives
- Political Figures
- High-Net-Worth Families
- Athletes
- Entertainers
- Celebrities
- Dignitaries
Each person identified in the above categories should, at minimum, have a light implementation of a Digital Executive Protection Program. Some other factors to consider when building a DEP are risk tolerance, exposure level, size of inner-circle, and historical threat factors.
Who should build a DEP program
DEP Programs are typically run by corporate and family office security teams. Each entity will have its own structure and “role” to identify to own the program. Usually, it is the same role that owns the executive protection program however, it can assign itself (around 25%) to the cybersecurity department as the majority of DEP falls into “digital.”
Some roles we work with at 360 Privacy regarding DEP programs:
- Chief Security Officer
- Chief Information Security Officer
- Head of Protection Services
- Head of Protective Intelligence
- Head of Cyber Operations
- Contracted Security Program Lead
The type of organizations building and deploying DEP programs:
- F500 and High-Growth Organizations
- Family Office and Multi-Family Office
- Foundations and Non-Profits
- Athletes, Entertainers and Celebrities
- Wealth Management, Venture Capital, and Private Equity
- Military and Federal Programs
Building the Program
An at-a-glance look at building the program:
- Conduct a threat landscape assessment
- Define program objectives
- Operational objectives
- Cross-team communications – how to alert and send routine reports?
- Incident response – how to handle security incidents?
- Continuity plan – How to keep operations moving during an incident?
- Privacy objectives
- Footprint reduction – what is findable online?
- Device & app privacy settings – what information is being gleaned from devices?
- Cybersecurity objectives
- Device security and encryption – how hackable are devices?
- Access control – who can access what accounts?
- password management – are passwords complex and non-rememberable?
- Secure Communications Protocols – Encrypted and redundant communication methods?
- Operational objectives
- Conduct a gap assessment
- Defining policies and procedures
- Assemble a team and vendor
- Testing and improvements
Conduct a Threat Landscape Assessment
The first step in building a digital executive protection program is to conduct a thorough assessment of the threat landscape. This involves identifying potential threats:
- Cyber Attacks
- Data Breaches
- Social Engineering
- Insider Threats
- Financial Fraud
- Identity Theft
Additionally, this assessment should consider factors such as their roles, responsibilities, access privileges, and the sensitivity of the information they handle. Industry-specific risks and the organization’s profile should also be taken into consideration. By understanding the threats faced, you can develop an effective strategy to mitigate them.
Objectives
Clearly defined program objectives are essential for guiding the development of a digital executive protection program. Objectives may include protecting sensitive information, ensuring secure communication channels, preventing unauthorized access to executives’ devices, minimizing the impact of cyber incidents. These objectives should align with the organization’s overall security goals and executive leadership team’s requirements.
Operational Objectives
- Cross team communications
- How are you connected to program’s stakeholders?
- Is it widely adopted?
- Is it secure?
- Incident response plan
- Can you lean on existing procedures?
- Does it cover all threat types in your threat landscape (threat model)?
- Has it been rehearsed, tested, or used within the last year?
- Continuity Plan
- Redundancy for all things – communications, tracking, file storage, devices
Privacy Objectives
- Footprint reduction – how can threat actors research my executive?
- Data Brokers
- Public records
- Online magazines and Blogs
- Social Media
- Device & app privacy settings – what information is being gleaned from devices?
- Location tracking, online activity, pattern tracking
- App settings – How to secure social media accounts
Cybersecurity Objectives
- Device security and encryption
- Hard drive encryption
- Access control – who can access what accounts?
- Is a password manager adopted and used?
- Is there a record of account access, with regular audits?
- Secure Communications Protocols – Encrypted and redundant communication methods?
- Secure messenger
- Secure radio systems
Developing robust policies and procedures is vital for guiding the behavior of the executive leadership team and minimizing risks. Policies should cover areas such as password management, access controls, encryption standards, incident response protocols, and safe use of digital assets. Additionally, procedures should outline steps for:
- Reporting Incidents
- Handling Sensitive Information
- Conducting regular security awareness training with both the executive, executive family, and the support staff
Gap Assessment
A gap assessment should be made from what existing protections are enabled, if any, and what needs to be set up and configured. Consider your program requirements and what people, process, and technologies will be vital to meet those obligations, based on your starting point.
Some questions to ask:
- Do you have the right personnel in-house without hiring?
- Can this be an additional duty?
- How will this impact current day-to-day operations?
- Do you need additional technology?
- Data broker removals, dark web monitoring, device security?
- Do you have existing processes to build from?
Building a Team
To successfully implement a digital executive protection program, assembling a cross-functional team is crucial. This team should consist of experts from various fields, such as:
- Information Security
- Threat Management
- Protective Services
- Protective Intelligence
- Executive Support Staff
Collaboration among team members ensures comprehensive coverage and a holistic approach to protection. Lean on the experts throughout the process, as collaboration makes a good program a great program.
Define Security Polices
Deploying appropriate education and technical solutions forms the backbone of a digital executive protection program. Develop a set of security policies specifically tailored to protect the executive leadership team. These policies should encompass areas such as device usage, data access and handling, communication protocols, password management, social engineering awareness, PII scrubbing, residential obfuscation, and dark web monitoring.
Review Existing Policies and Procedures
Examine the current security policies, procedures, and guidelines in place within the organization. Identify any relevant policies that already address device usage, data access and handling, communication protocols, password management, social engineering awareness, PII (Personally Identifiable Information) scrubbing, residential obfuscation, and dark web monitoring.
Communication and Awareness
Clearly communicate the new executive-facing security policies to all executives, relevant stakeholders, and other employees who interact with executives. The success of any DEP Program depends on the level of buy-in from the team surrounding the protected.
Example Policies:
Secure Remote Access: Establish secure remote access protocols to allow the executive team to work from anywhere while maintaining the necessary security measures. This may involve using secure virtual private networks (VPNs) and remote desktop solutions that adhere to stringent security standards.
Device Security: Deploying endpoint protection solutions, such as antivirus software, firewalls, and mobile device management tools, to secure executives’ devices against malware, unauthorized access, and data leakage.
Strong Authentication: Enforce strong authentication measures to ensure only authorized individuals can access executive accounts and devices. This includes implementing multi-factor authentication (MFA) for all relevant systems and applications.
Password Policy: Enforce a password policy that requires complex, unique passwords and regular password changes. Encourage the use of password managers to securely store and generate strong passwords.
Phishing and Social Engineering Awareness: Provide training and education to the executive leadership team, executive families, and executive support staff on recognizing and mitigating phishing attempts and social engineering attacks. This will help them develop a security-conscious mindset and prevent inadvertent disclosure of sensitive information.
Network Security: Establishing robust network security measures, including intrusion detection systems, firewalls, and regular vulnerability assessments, to safeguard against external threats. High quality network equipment makes home network security configurable to meet even the most stringent requirements. Brands such as Ubiquiti and Meraki are ideal for home networks of high-profile individuals.
Data Protection: Enforcing data encryption, data loss prevention (DLP) mechanisms, and access controls to protect sensitive information from unauthorized disclosure or theft.
Continuous Monitoring: Implement a comprehensive monitoring capability that continuously monitors the executive leadership team’s digital activities for potential threats. This may include intrusion detection systems, log analysis, and threat intelligence feeds to proactively identify and respond to any suspicious or malicious behavior. In some cases, existing tools can be retooled to monitor for threats specific to executives and leadership.
Ongoing Training and Awareness: Conduct regular security awareness training sessions and keep the executive team updated on emerging digital threats and best practices. Encourage a culture of security consciousness within the organization to ensure everyone understands their roles and responsibilities in protecting sensitive information.
Regular Auditing and Testing: Periodically conduct audits and penetration tests to assess the effectiveness of the Digital Executive Protection program. Identify any gaps or vulnerabilities and take corrective actions accordingly.
Partner with Experts: Consider partnering with external security experts or specialized vendors who can provide additional insights, expertise, and tools to enhance the security posture of the executive leadership team. These experts can help with threat intelligence, incident response, and ongoing security consultations.
Education
Raising awareness among the executive leadership team, executive families, and executive support staff about digital threats and best practices is crucial. Conducting regular digital hygiene and awareness training sessions helps to educate executives, executive families, and executive support staff on phishing attacks, social engineering tactics, safe browsing habits, and the importance of strong passwords. Such training empowers them to make informed decisions and strengthens the overall security posture.
Testing and Continuous Improvement
Regular testing and evaluation of the digital executive protection program is critical to ensure its effectiveness. We recommend annual intervals (at a minimum) with spot checks after major implementations or upgrades. There are several different options to test a DEP program:
- Internal tabletop walkthroughs – use the internal team to develop and walk through scenarios based on your threat landscape assessment.
- Vulnerability assessments – leveraging topical SMEs, find the weakness in the program, from device security to communication hiccups
- Penetration testing – For more mature programs, use a “red team” to attempt to exploit and access your protected assets.
- External tabletop walkthroughs – Leverage an external vendor to conduct a tabletop exercise with all your DEP resources participating for a true, cross-team maturity assessment.
Based on the findings of the exercises, necessary adjustments can be made for a cadence of program enhancements.
Putting It All Together
By now, an outline of a Digital Executive Protection Program should be forming that fits your organization’s use case and resources. There is no “one-size-fits-all,” as every organization has different requirements, from resources to threats and everything in between.
360 Privacy’s Outsourced Digital Executive Protection
360 Privacy’s Digital Executive Protection, 360 Concierge, helps organizations easily stand-up a customizable DEP program with fast results and a seamless onboarding process.
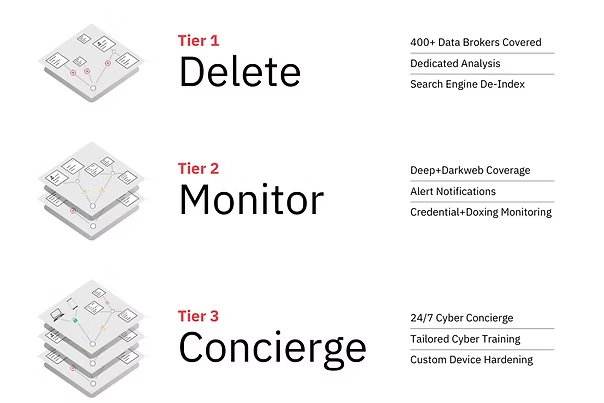
Digital Protection, Tailored to your Organization
360 Privacy’s solutions make it easy for organizations to start small and build a program overtime, or implement a fully outsourced Digital Executive Protection program in a matter of days. Our tiered options present security leaders with flexible protections to fit their needs.
360 Privacy combines industry leading expertise and advanced technology to provide the top digital protection solution for executives, high-net-worth families, athletes, and entertainers. Our solutions include data broker removal, deep and dark web monitoring, device security and 24/7 digital security concierge. Regardless of the size of your organization’s security team, 360 Privacy enables all teams to implement a tailored digital protection program for those they protect.
360 Privacy: The Human Element
360 Privacy’s solutions enhance your organization’s digital protection. With over 200 years of experience navigating threat actors within Special Operations, Protective Services, Law Enforcement, and the Intelligence Community our team is pioneering Digital Executive Protection across all industries and organizations, constantly responding to the dynamic threat landscape. Operators, analysts, linguists, engineers, and agents all work together to uncover unique threats and deliver unparalleled digital protection to some of the world’s largest brands and household names.
Interested in learning more about 360 Privacy?
About the Authors
Trinity Davis
Trinity Davis boasts an 18-year tenure in the Executive Protection Industry, during which he has expertly cultivated and guided cross-functional teams. His unwavering commitment has been pivotal in safeguarding the security and privacy of executives and their families across diverse sectors, including private industry, Social Media, FinTech, and the Private Family Office Space. Through his exceptional leadership, he has consistently ensured the highest standards of safety and confidentiality, earning trust from those he has been charged with protecting, and peers alike.
Gavin Quinn
Gavin Quinn is a seasoned professional with a broad background encompassing Special Operations, F100 Cyber Operations, and a thriving Tech Security Startup. With over a decade of experience, he excels in constructing comprehensive security programs and adeptly connecting cyber and physical security teams to ensure a well-rounded and robust security approach.

